
Using patterns to verify identity could enhance computer security.
If there’s one thing that should be learned by everyone with the most recent hacking fiasco of Wired’s Mat Honan, passwords aren’t secure. A team of researchers from Stanford and Northwestern universities, as well as SRI International, have been experimenting with security to use the brain’s innate ability to learn and recognize patterns.
The researchers presented their findings at the 2012 USENIX Security Symposium in Bellevue, Washington in August. The main goal of the scientists was to study ways of covertly storing secret data within the brain’s corticostriatal memory system, which is part of the neural architecture that reminds us how to do things.

In order to test their thesis, the researchers created a computer game that required players to tap buttons on a keyboard as large black dots descended across a horizontal line. It’s akin to Guitar Hero. The initial training session lasted between 30 minutes to an hour, and the dots fell at different speeds in various locations, forming patterns that were repeated until the participants became adept at hitting the right buttons at the right time.
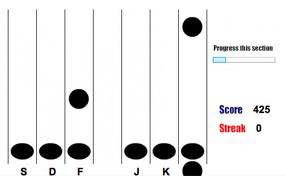
Game used to train brain
The users’ corticostriatal memory became adept at repeating the patterns, which is analog to dialing a phone number or typing a word on a keyboard without looking at your fingers. This serial interception sequence learning can be used later to confirm a person’s identity. The participants cannot be coerced to reveal this since they had no conscious knowledge of it.
Thus, users cannot be forced or tricked into revealing a password. 370 players were tested so far, and more participants continue to be added. Web-based email services could not rely on something like this for added security, but high-security installations, run by the government, could definitely implement this for added security.
Since the authentication sequence has to be stored somewhere, hackers could break into databases and still get user information; however this was designed to address the problem of coercion.









Be the first to comment on "Verifying Identity With Patterns Could Make Computers More Secure"